- collaboration
Invite Team Members
Assign Projects
Users & Role Management
Review Management [Test Cases]
Review Management [Elements]
Execution Controls
- test cases
Test Cases
Test Case List Actions
Import and Export Test Cases
Import Test Project Test Cases
Importing Postman Collections and Environments
Test cases for Desktop Windows
Update Test Case result in a Test Plan
Test cases for Mobile Web Application
- Test Step Types
Type: Natural Language
Type: REST API
Type: Step Group
Type: For Loop
Type: While Loop
Type: Block
Type: If Condition
Nested Step Groups
Create Test Steps
Image Injection
Cross-application testing
- Test Data Types
Raw
Parameter
Runtime
Random
Data Generator
Phone Number
Mail Box
Environment
Concat Test Data
Create Test Data [Parameter]
Update Test Data Profile
Updating Value in TDP
Import TDP
Bulk Deletion of a Test Data Profile
Create Test Data [Environment]
- Elements (Objects)
- Web Applications
Record Multiple Elements
Record Single Element
Create Elements
Supported Locator Types
Formulating Elements
Shadow DOM Elements
Verifying elements in Chrome DevTools
Handling iframe Elements?
Dynamic Locators using Parameter
Dynamic Locators using Runtime
Using Environment Test Data for Dynamic locators
Import/Export Elements
AI Enabled Auto-Healing
- test step recorder
Install Chrome Extension
Install Firefox Extension
Install Edge Extension
Exclude Attributes/Classes
- test plans
Add, Edit, Delete Test Machines
Add, Edit, Delete Test Suites
Schedule Test Plans
Run Test Suites In Parallel
Cross Browser Testing
Distributed Testing
Headless Testing
Test Lab Types
Disabling Test Cases in Test Plans
AfterTest Case
Post Plan Hook
AfterTest Suite
Email Configuration in Test Plan
Execute Partial Test Plans via API
Ad-hoc Run
Test Plan Executions
Dry Runs on Local Devices
Run Tests on Vendor Platforms
Run Test Plans on Local Devices
Test Locally Hosted Applications
Debug Test Case Failures
Parallel and Allowed queues
- debugging
Debug results on local devices (Web applications)
Debug Results on Local Devices
Launch Debugger in the Same Window
- Testsigma Agent
Pre-requisites
Setup: Windows, Mac, Linux
Setup: Android Local Devices
Setting up iOS Local Devices
Update Agent Manually
Update Drivers Manually
Delete Corrupted Agent
Triggering Tests on Local Devices
- troubleshooting
Agent - Startup and Registration Errors
Fetching Agent logs
Upgrade Testsigma Agent Automatically
Testsigma Agent - FAQs
- continuous integration
Test Plan Details
REST API (Generic)
Jenkins
Azure DevOps
AWS DevOps
AWS Lambda
Circle CI
Bamboo CI
Travis CI
CodeShip CI
Shell Script(Generic)
Bitrise CI
GitHub CICD
Bitbucket CICD
GitLab CI/CD
- desired capabilities
Most Common Desired Capabilities
Browser Console Debug Logs
Geolocation Emulation
Bypass Unsafe Download Prompt
Geolocation for Chrome & Firefox
Custom User Profile in Chrome
Emulate Mobile Devices (Chrome)
Add Chrome Extension
Network Throttling
Network Logs
Biometric Authentication
Enable App Resigning in iOS
Enable Capturing Screenshots (Android & iOS)
Configure Android WebViews
Incognito/Private mode
Set Google Play Store Credentials
- addons
What is an Addon?
Addons Community Marketplace
Install Community Addon
Prerequisites(Create/Update Addon)
Create an Addon
Update Addon
Addon Types
Create a Post Plan Hook add-on in Testsigma
Create OCR Text Extraction Addon
- configuration
API Keys
- Security(SSO)
Setting Up Google Single Sign-On(SSO) Login in Testsigma
Setting Up Okta Single Sign-On Integration with SAML Login in Testsigma
Setting up SAML-based SSO login for Testsigma in Azure
iOS Settings
Creating WDA File for iOS App Testing
- uploads
Upload Files
Upload Android and iOS Apps
How to generate mobile builds for Android/iOS applications?
- Testsigma REST APIs
Environments
Elements
Test Plans
Upload Files
Get Project wide information
Upload and update test data profile
Trigger Multiple Test Plans
Trigger Test Plan remotely and wait until Completion
Run the same Test Plan multiple times in Parallel
Schedule, Update and Delete a test plan using API
Update Test Case results using API
Create and update values of Test Data Profile using REST API
Rerun Test Cases from Run Results using API
- open source dev environment setup
macOS and IntelliJ Community Edition
macOS and IntelliJ Ultimate Edition
Windows and IntelliJ Ultimate Edition
Setup Dev Environment [Addons]
- NLPs
Unable to retrieve value stored in text element
Unable to capture dropdown element
Unable to Select Radiobutton
Unable to Click Checkbox
- setup
Server Docker Deployment Errors
Secured Business Application Support
Troubleshooting Restricted Access to Testsigma
Why mobile device not displayed in Testsigma Mobile Test Recorder?
Unable to create new test session due to unexpected error
- web apps
URL not accessible
Test Queued for a Long Time
Issues with UI Identifiers
Missing Elements in Recorder
Collecting HAR File
- mobile apps
Failed to Start Mobile Test Recorder
Troubleshooting “Failed to perform action Mobile Test Recorder” error
Test Execution State is Queued for a Long Time
Mobile app keeps stopping after successful launch
More pre-requisite settings
Unable to start WDA Process on iPhone
Most Common causes for Click/Tap NLP failure
Finding App Package & App Activity (Android)
- on premise setup
On-Premise Setup Prerequisites
On-Premise Setup with Docker-compose File
Post-Installation Checklist for On-Premise Setup
Install Docker on an Unix OS in Azure Infrastructure
SMTP Configuration in Testsigma
Configure Custom Domains
- salesforce testing
Intro: Testsigma for Salesforce Testing
Creating a Connected App
Creating a Salesforce Project
Creating Metadata Connections
Adding User Connections
Build Test Cases: Manual+Live
Salesforce Element Repositories
Intro: Testsigma Special NLPs
Setting Up Okta Single Sign-On Integration with SAML Login in Testsigma
Single Sign-On (SSO) provides faster, easier, and trusted access to applications.
With SSO, you are not required to store and manage passwords for the websites you use regularly. Instead of using passwords, applications that allow SSO login accept secured tokens that grant access to the application. This is mostly used for enterprises and SMBs for easy workforce identity management.
You can enable Single Sign-On (SSO) in Testsigma with Okta. Once configured, you can log into your Okta Dashboard to see your SSO-supported applications, including Testsigma. Okta will verify the user's identity and permissions, and then grant them access to Testsigma.
Terminology
Here are a few entities that you need to be aware of before we move on to the details:
| A user | The person requesting access to the service. In this case, Testsigma App User |
|---|---|
| A service provider(SP) | The application that provides the service or protects the resource. In this case, Testsigma App |
| An identity provider(IdP) | The service/ repository that manages the user information. It may be Okta, Onelogin, Azure AD, or an in-house IdP/IAM Implementation |
| Entity ID | Entity ID is an identifier(an alphanumeric string or URI given by the Service Provider (SP) that uniquely identifies it. It's often part of a metadata file (an XML file with a certificate, entity ID, and endpoint URLs). You would get this from the IP (Okta, Onelogin e.t.c). |
I. Getting the Testsigma Configuration for Okta
Navigate to Settings > Security

The security page looks as shown below if SSO has not been enabled yet:
If you are interested to know how you can set up Google SSO with Testsigma, refer here.
You will see two options here - Google and SAML. Choose SAML and click the Proceed button.
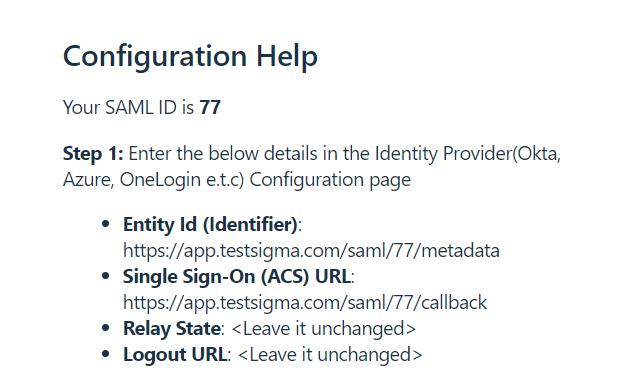
You will find all the details you need to enter in Okta here as shown below: The important ones are ‘Entity ID’ and ‘Single Sign-On(ACS) URL’(refer to the Terminology section). Note these down to use in the next section - section II.
II. Create and configure OKTA
We strongly suggest you check with your IT team before trying the below steps since they might have exclusive admin access to the IdP configuration.
-
Navigate to https://www.okta.com/login and login to the Admin console in OKTA.
a. In the Admin Console, under Applications, click Create App Integration to get the Create a new app integration form as shown below:
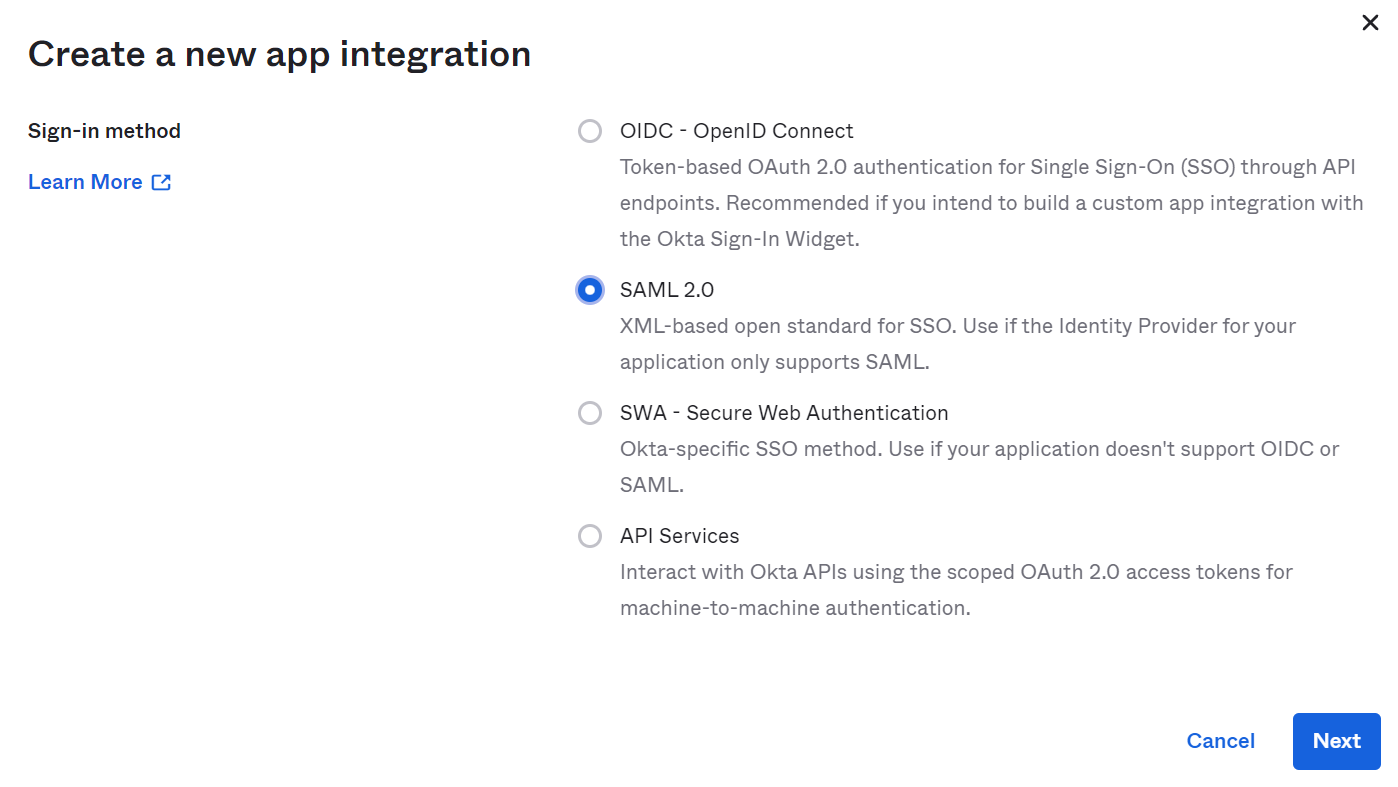 b. Choose SAML 2.0 and click Next
b. Choose SAML 2.0 and click Next -
On the first page - General Settings, you need to enter the details of the application (Testsigma) that you are integrating with SAML.
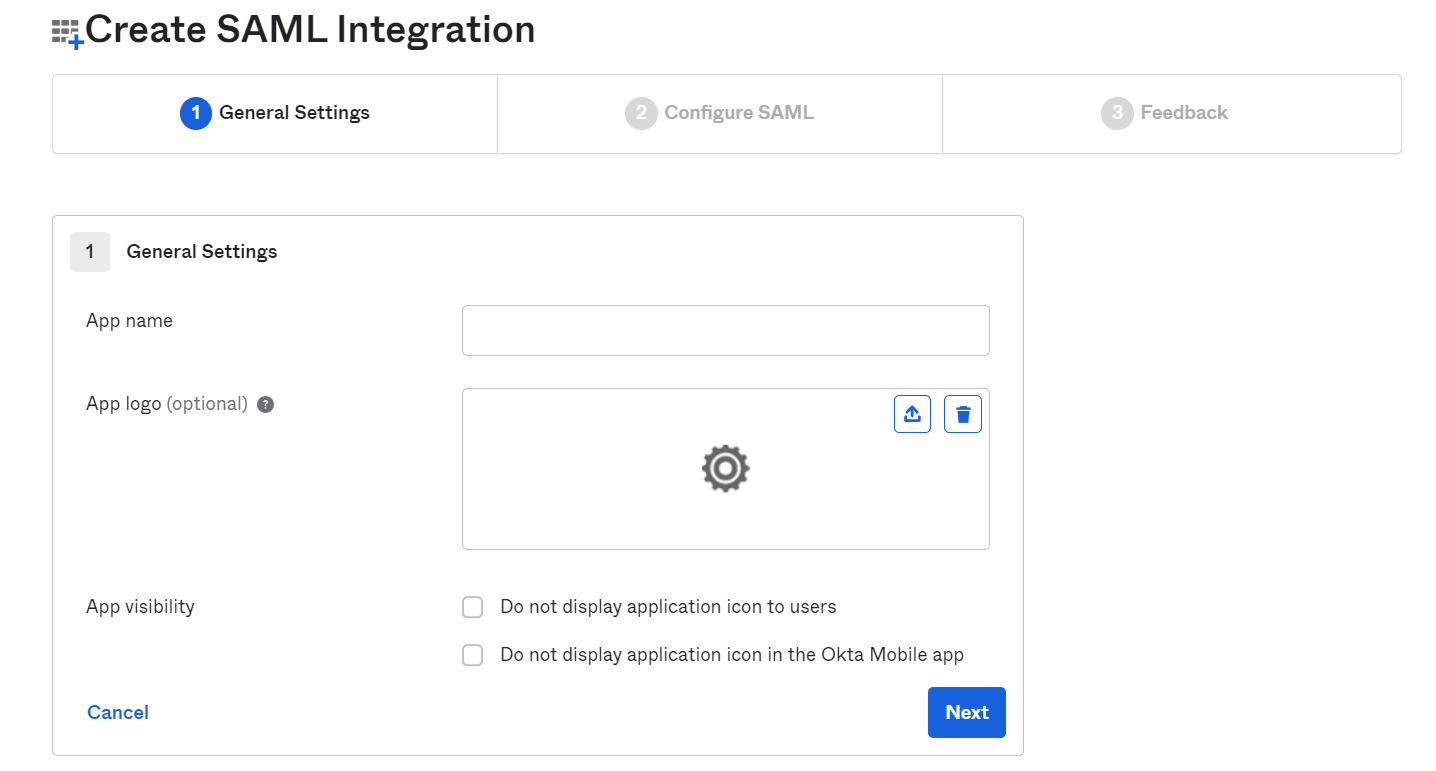
a. App Name: Enter the application name, “Testsigma”, upload the logo (if required)
b. App logo and visibility: Upload the app logo if you prefer. (You may choose to display or not display the icon of Testsigma to the users in the Okta app for both web and mobile)
Click on Next to proceed.
- On the second page - Configure SAML, we need to provide the Configuration details we got from Testsigma App following the steps in section I.
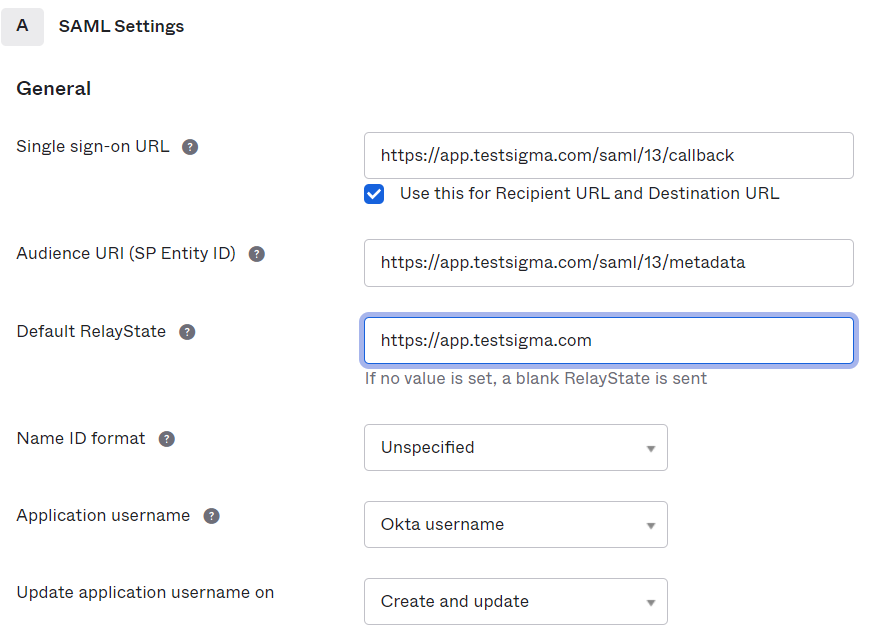 a. Single Sign-on URL: https://app.testsigma.com/saml/77/metadata
a. Single Sign-on URL: https://app.testsigma.com/saml/77/metadata
b. Audience URI: https://app.testsigma.com/saml/77/metadata
c. Default Relay State : https://app.testsigma.com
d. Name ID Format : EmailAddress (default)
e. Application Username : Okta username (default)
f. Update application username on: Create and update (default)
- On the next page, check the options, “I'm an OKTA User and adding an Internal App” and “This is an internal app that we have created” and click Finish.
- Next, you will see a Sign-on methods page. The sign-on method determines how a user signs into and manages their credentials for an application.
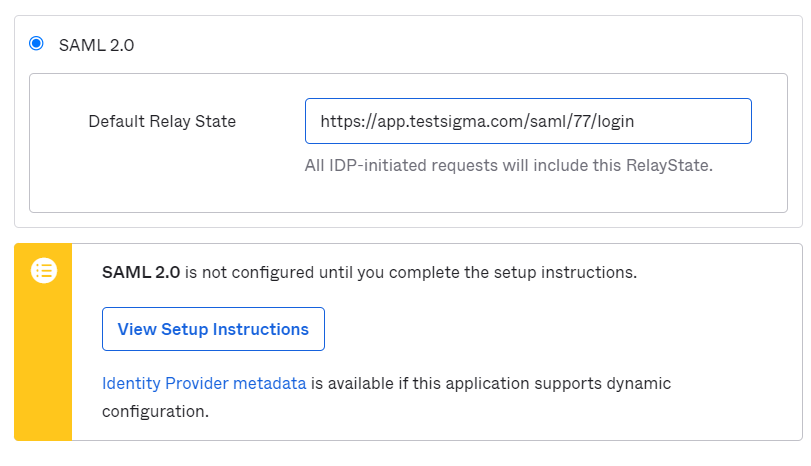 a. Click on 'View Setup Instructions'
a. Click on 'View Setup Instructions'
b. Copy and note down the 'Identity Provider Issuer', 'Identity Provider Single Sign-On URL', and 'X.509 Certificate' from this page. We will need the same on the Testsigma SAML SSO Configuration page in the next section - Section III.
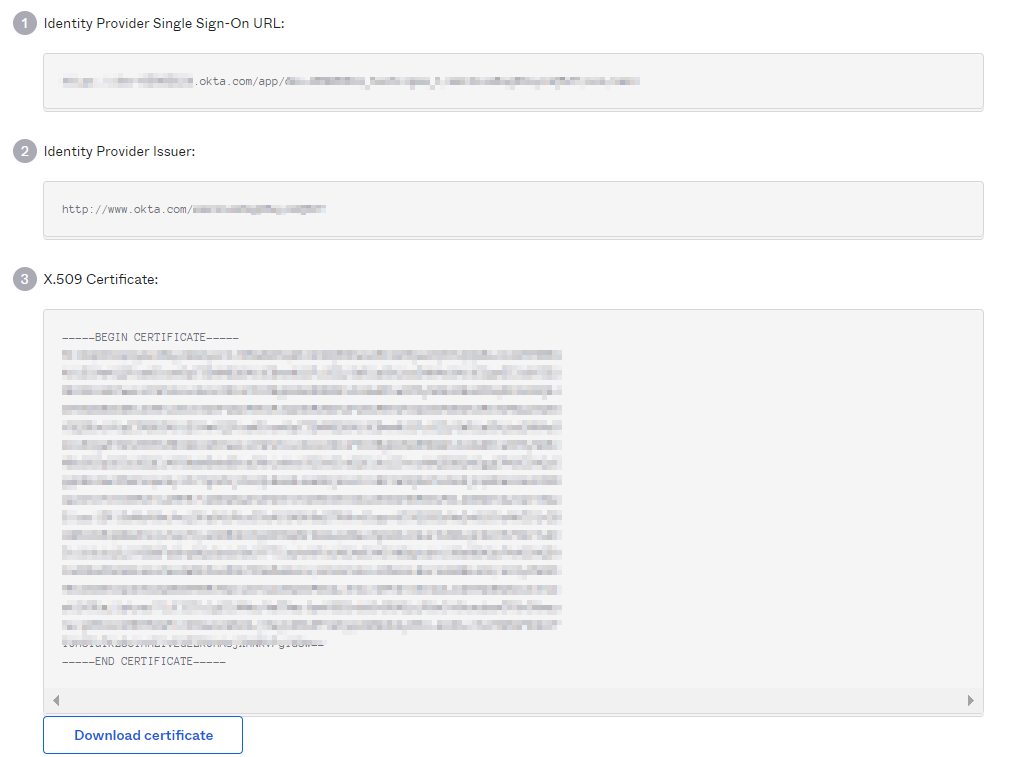
Now, let's move on to the configuration that we need to perform in the Testsigma App.
III. Configuring Testsigma for Okta
You would need to enter the Entity ID, SSO URL, and SAML Certificate you got from the last step (Step 5. b) in the previous section.
You may notice some differences in the terminologies used within Testsigma and Okta.
- Entity Id (Identifier) is the same as Identity Provider Issuer
- Identity Provider Single Sign-On URL is same as Single Sign-On (ACS) URL
- SAML Certificate is referred to as X.509 Certificate in Okta
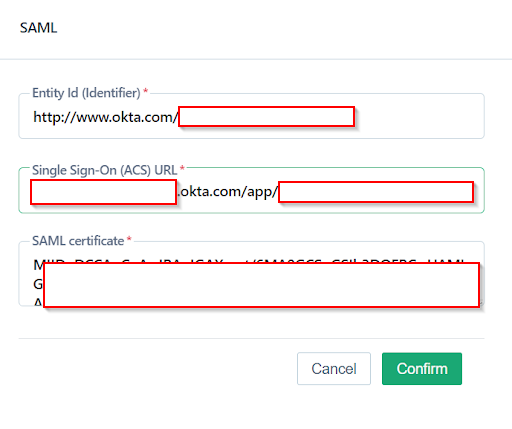
Enter the details and click Confirm.
And, you are done.
To disable the SSO login using Okta, click the Disable button on the SAML option anytime.
After this, every user in your account would need to log in to Testsigma via the Okta Dashboard once logged out from the current session.